DDoS
A DDoS attack (Distributed Denial of Service) is an attack on a web server with the intent of causing it to crash. While a DoS attack is usually carried out by just one computer, the high impact of a DDoS is achieved by joining many computers into a botnet in order to provoke the server failure. For this purpose, manipulated IP packets are usually sent en masse to the server simultaneously. DDoS attacks are used by both cybercriminals and protest movements such as Anonymous.
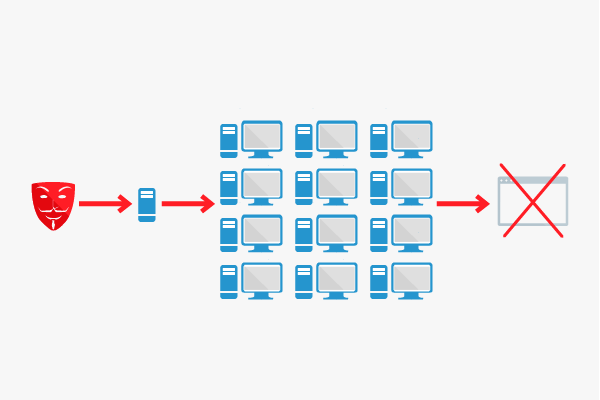
How it works
To produce a DDoS on a server, as many computers as possible have to be involved in the attack. For this purpose, other computers are infected with malware that allows attackers to hijack them and use their computing power for their own purposes. Computer viruses that spread themselves are frequently used. The infected computers will eventually turn into bots, which can be coordinated from a central location. In order to hide the controlling computer, additional tools are used in DDoS attacks which permanently change the corresponding IP addresses. Therefore, the author of an attack usually remains undetected.
Once enough computers are combined to form a network, the attack is launched against the target server.
Types
A DDoS attack can be carried out in various ways, but there are generally three types:
- Overloading the server resources: In this case, the resources of the target system are so overloaded that the server cannot answer any more queries.
- Overloading the bandwidth: This attempts to overload the entire capacity of the network so that the target website is no longer accessible.
- Exploit: By exploiting vulnerabilities in the server or website software, the attackers try to control the targeted server using a DDoS.
- Creation of unexecuted requests (SYN Flood): A TCP function is used with which the recipient confirms for the server that a data packet has been received.
Possible protective measures
A DDoS shows up existing overloads of a server system or network, but the effect of such an attack is potentiated. The following measures can be taken to minimize the damage:
- Blocking of IP addresses: If the firewall of the server recognizes suspicious IP addresses, access to the server can be denied. These addresses can be manually stored and dynamically generated. Corresponding filters can be installed via the provider.
- Filtering of invalid IP addresses: By filtering out invalid IPs, the provider’s border router can prevent attackers from being able to circumvent such lists of blocked IP addresses.
- Use of server clusters or Content Delivery Networks that help to minimize the server load.
Possible motives
The primary goal of a DDoS attack is to make a website inaccessible. Thus, the information it contains is no longer reachable. For online stores or other commercial websites such as payment service providers, this could mean huge financial losses. Moreover, victims of hacker attacks usually are stigmatized as being not secure. Losses in reputation and trustworthiness are the result.
In the past, DDoS attacks were mostly carried out based on two possible motives:
- Protest
- Extortion
While in the first case, politically motivated groups were often behind the attacks, the second scenario concerns criminals.
One of the most well-known protests which was expressed in a large-scale DDoS attack in recent years was “Operation Payback,” which was initiated by the hacker group “Anonymous.” The target of the attack was the payment service PayPal, which had not forwarded donations to whistle-blowing platform WikiLeaks.
A more recent example of a criminal use of controlled network attacks is the extortion of the RSS feed provider Feedly.
Web Links