Hijacking
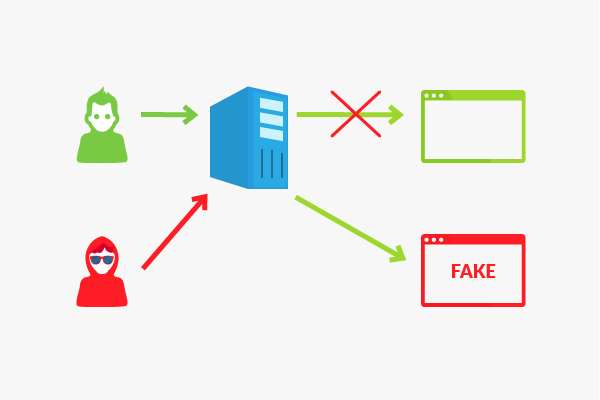
Hijacking is an attempt to take over a specific element from the Internet environment through unauthorized routes. Besides URL hijacking, there is domain, DNS, browser, TCP, session hijacking and more.
Browser hijacking
Browser hijacking is usually done through a very small software program on the computer that is not noticeable due to its size. This program overwrites the default functions of a web browser without the user’s authorization and knowledge. Removal of this kind of software usually involves a lot of effort.
How it might work
- The home page of the affected browser is overwritten. The user is then automatically directed to the website of the hijacker when he starts his browser.
- The search engine does not show the regular ranking, instead it is redirected to the hijacker’s search engine page. The hijacker earns money on this page through advertising.
- When you attempt to access a particular shopping site, a page that belongs to an advertiser associated with the hijacker will be displayed instead, without you noticing it.
Prevention
For such a software to ever be installed on a computer requires first an OK from the owner. This is unknowingly given when you click on OK in a pop-up window. Such windows may also include fake security alerts that a user intuitively wants to click off with OK. To prevent such software from being installed on your computer you should always first briefly examine the pop-up window. If in doubt, never click OK.
Domain Hijacking
In domain hijacking, a domain is illegally taken over from the rightful owner. Its most aggressive form is domain theft. Such scammers often get access to the domain registry through identity theft. The hijacker assumes the identity of the rightful owner and modifies the registry information to reallocate the domain to himself and thus steals it. Some registration services act quickly when fraud of this kind is noticed. However, it also happens that action is taken only when it is enforced by law. In some cases, the hijacker may retain control over the domain. Victims mostly do not have the will or the financial means to go through lengthy and time-consuming legal proceedings that would return the domain back to them. The fact that hijackers act in another country is a deterrent as well. Meanwhile, the hijacker has full control over the domain and may freely dispose of content or redirect HTTP status codes.
Prevention
In many domain registries, there is a possibility to work with a special authentication code which is known only to the owner of the domain. This gives protection against unauthorized access.
Contrast to the legal acquisition of expired domains
Domain hijacking must not be confused with the acquisition of expired domains. In the latter, the value of expired domains is utilized. A short time after the expiration of a domain or its deletion, there are still backlinks, PageRank, and trust. This makes the domain valuable as it means that a lot of traffic is still coming to it. Providing the search engines don’t detect that the website has new content, their new owners can cash in. Over time, such a website loses its value, however. Such expired domains can be purchased legally.
Content Hijacking
In content hijacking, the content of other websites is issued as one’s own. This is done through duplicate content which will be detected by search engines eventually, however. Another way is to integrate a condensed version of existing content into your website which is partially automated. Such content theft may have the consequence that the webpage with the original content loses PageRank, while the page with the stolen content appears higher in the search results. The latter thus gets more traffic and can be profitable, for example, through online advertising.
DNS hijacking
In DNS hijacking, an attacker interposes himself as a man-in-the-middle between the DNS client and DNS server. In this position, he can intercept, read, and manipulate all messages.
URL hijacking
In URL hijacking, a page is incorrectly removed from the search engine ranking and replaced with a page linked to it. More on that in the article on URL Hijacking.
Network hijacking
In network hijacking, an insecure server which is part of an intranet, wireless local area network (WLAN), or a similar network is taken over. Frequently the actual owner of the server gets locked out.
Typing-error hijacking / type-writing hijacking
Typos of searchers are exploited in this case. Frequently incorrectly spelled versions of well-known websites are used to direct you to a different page. Thus, the hijacker can benefit from the prominence of the website.
Search engine hijacking
Search engine hijacking can happen with browsers that offer a separate field for search engines so you don’t have to separately call up the corresponding website. In the past it happened that the search engine was unnoticeably changed to another with keyword.URL. In response, Mozilla made changes to version 19 and 20 of the Mozilla Firefox web browser at the end of 2012. Users must first confirm a modification of the default search engine.
TCP hijacking
TCP Hijacking refers to the acquisition of a foreign TCP connection. The target can be to take over the connection and simultaneously take down a communication partner. On the other hand, the connection may be maintained to inject instructions.
Session hijacking
Session hijacking refers to the exploitation of a valid session. To this end, the session ID must be stolen, which can be done by passive eavesdropping when it is sent to the other server via cookies in many applications. As long as the session ID is valid, the attacker has control of the session and may use or abuse the application on behalf of the actual owner.
Prevention
- The basis of any data transmission on the internet should be an HTTPS connection, which encrypts the data using SSL, just as is the case with encrypted search. When data packets are intercepted, the content must be decrypted in order to get the session ID.
- Protection against cross-site scripting is also helpful. These prevent the smuggling of JavaScript code and the reading of cookies.
- Session IDs should not be included in the URL. These are stored in log files and can be easily read by attackers.